OkHello provides a free group video chat service. Its app is available on the App Store and on Google Play. If you’ve ever used it, your details may be in others’ hands right now.
According to their Privacy Policy, OkHello collects a lot of personal information about users, including geolocation data and information from Facebook if you use Facebook Connect to access their service.
Of concern, a lot of that personal information appears to have been inadequately secured, and at this point, DataBreaches.net does not know for how long personal details have been exposed or how many people may have downloaded them.
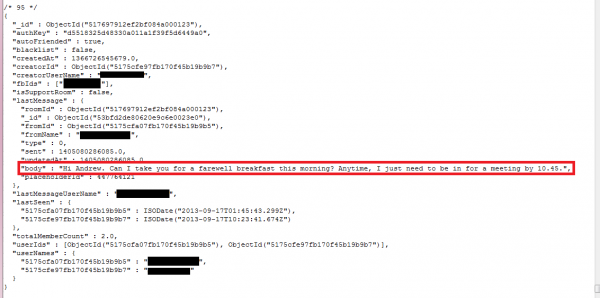
Earlier today, white-hat researcher Chris Vickery informed DataBreaches.net that 2,627,082 users’ account details have been exposed. No passwords or authentication are needed to view and download user details that include first and last names, password hash, Facebook IDs, phone number, email address, messages, and friends’ information. The screencaps below were taken from the database and were redacted by Chris. The second one – with the personal message – came from a table that has 8.2 million entries.
Chris says he discovered the leak because OkHello failed to secure their database on a port that is indexed by Shodan.
Not only could Chris access the database through that port, but he discovered that OkHello also has a web page that allows anyone to download the entire database backup without any login required. DataBreaches.net went to the IP address Chris provided and verified that the entire database – more than 9 GB – could be downloaded without any password.
In its privacy policy, OkHello claims to care about its users’ information security:
Keeping your information safe: OkHello cares about the security of your information, and uses commercially reasonable safeguards to preserve the integrity and security of all information collected through the Service. However, OkHello cannot ensure or warrant the security of any information you transmit to OkHello or guarantee that information on the Service may not be accessed, disclosed, altered, or destroyed.
Attempts to Notify Failed
Chris attempted to contact OkHello through their support portal yesterday, but received no response. OkHello has no phone number on their web site and their domain registration is protected. DataBreaches.net sent an alert to [email protected] this afternoon, but has received no response as yet. DataBreaches.net also attempted to reach their external counsel through Twitter to see if they could call them, and actually called the law firm’s Los Angeles office, only to be told by the weekend receptionist that he had no way of knowing who represented them and they wouldn’t be calling anyone.
While DataBreaches.net usually does not reveal a leak until after the entity has had time to secure it, in researching this incident, DataBreaches.net discovered that the leak had already been disclosed on Twitter by Jay Fuller, who also tried (unsuccessfully, it seems) to reach OkHello through their Twitter account.
Would this be an appropriate time to remind everyone that I have repeatedly called for sites to be required to provide a dedicated and monitored phone number or email address that can be used to alert them to security breaches?
In the meantime, if anyone knows any of the principals of OkHello and can pick up the phone and call them to tell them to secure their database, that would be nice.
Update Dec. 8: As of this morning, OkHello’s backup database is still freely available. I haven’t checked their current installation, but they haven’t responded to attempts to alert them. Tweets to the California Attorney General, OkHello’s external counsel, and FTC do not seem to have resulted in anyone contacting them to address this leak, which includes personal messages.
Update Dec. 14: OkHello’s live MongoDB database is still up and still leaking.
Update Dec. 15: See this post for what happened next.