On her web site, Patricia Mullen describes herself as a “behavior intervention specialist” and a former special education teacher. According to her site, she has
worked in many school districts and agencies throughout the state of Washington consulting and training. Patricia is also a national trainer having presented to hundreds of foster parents, teachers, and providers throughout the United States and Canada.
Also according to her web site, she has been in private practice for the past 15 years, working with multi-aged children and their families on behavior issues. Her practice is located in Spokane, Washington.
Given the nature of her work, I might expect that although she does not appear to be a HIPAA-covered entity, records she might create involving any school consultation on a specific child might be covered under FERPA.
On December 20, Chris Vickery notified DataBreaches.net that he had discovered a misconfigured MongoDB database with Mullen’s data in it. Her files included data on 258 clients.
The database was not Mullen’s, however. It appeared to contain data from clients of a firm that is no longer in business, ZyphMartin. Other ZyphMartin clients who had data in the database included CDA Realtors, Dr. Culings (a dentist), Energized Learning, Meadow Wood, Modern Drywall, OLP Contracting, Richardson’s Garage, Studio Fit, and Ugly Fish.
Multiple attempts to reach Ms. Mullen by phone and through her on-site contact form beginning on December 20 were unsuccessful. Attempts to track down ZyphMartin led me to Brandon Martin, a former partner who had left ZyphMartin approximately four years ago, he estimated, but who recognized Ms. Mullen’s name as a client at the time he was there. Martin informed DataBreaches.net that after he left ZyphMartin, Todd Zyph became Zyph Design Co., and eventually sold his business to Design Spike, Inc. Whether Ms. Mullen or the other clients continued on as clients of DesignSpike, Inc. is unknown to DataBreaches.net.
After Brandon Martin helpfully reached out to Design Spike, the leaky database was secured, but Will Hall of Design Spike did not respond to several e-mails from DataBreaches.net asking questions about the database and whether Ms. Mullen and the others had been clients of Design Spike and/or were currently clients. The Design Spike web site does not list any of them in their list of clients.
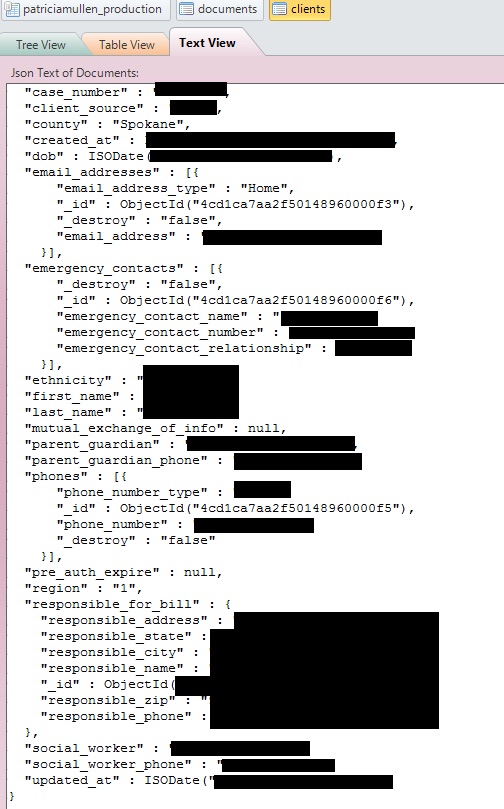
As can be seen in a screen shot of an entry in Ms. Mullens files below, the personal information collected includes referring source, name, date of birth, ethnicity, e-mail address, emergency contact information, the name and phone number of the parent or guardian, information on the party responsible for the bill, the name of any social worker involved in the case and their phone number. Other files and documents are not being included in this report because they also contained personal information and reports.
That the database was the responsibility of Design Spike, Inc. seems very likely from the sequence of events and that when notified by Brandon Martin, the database was then secured.
But why didn’t Ms. Mullen respond to repeated attempts to alert her that her client data was exposed? Realizing that her web site copyright date was 2014, I had to consider the possibility that she might be ill, that the site may be an abandoned site, or that she might even be dead. There were no upcoming events listed on her calendar and a Google search on her name turned up no recent results.
And that led me to thinking about whether enough of us have made arrangements with others to secure or remove our data in the event something happens to us. I hope Ms. Mullens is okay, but if she is, then why didn’t she respond to multiple notifications? And did she ever know that her client data was (still) in a database under the control of Design Spike. Do the other clients know? Has Design Spike notified them? There are many unanswered questions.
And one of the most important questions is: if these entities were no longer clients of Design Spike, why was their data still online?