December appears to have been a rough month for Blue Cross Blue Shield of Michigan. Yesterday, I discovered that they had a second breach that was disclosed last month, although it seems to have flown under most media radar.
The first breach, fairly widely reported already, involved a laptop stolen from a subsidiary’s employee that held data on 15,000 policyholders. But that same week, one of the health insurer’s service providers was also sending out notifications to an unspecified number of policyholders. Wolverine Solutions’ notification template, reproduced below, explained that on September 23, they experienced a ransomware incident. Their investigation did not indicate that any data had been exfiltrated, but as is often the case, they couldn’t totally prove that it hadn’t been.
On November 8, 2018, we notified our client that we identified data in our systems that included demographic information, health plan contract numbers and some medical information. Some data also included Social Security numbers. We are alerting you because your data may have been affected.
You can read the full notification below. Wolverine Solutions informed those affected of some complimentary services to help them:
WolverineSolutions_BCBSMIWe have arranged for affected individuals to have AllClear ID protect their identity for 12 months at no cost. However, due to Blue Cross Blue Shield of Michigan’s policy, special arrangements have been made to offer you the same protection for 24 months.
The University of Michigan reported that 70 of their employees who were covered by the BCBS of Michigan health plan were affected by the breach. It is not clear how many non-university policyholders were affected and this incident does not (yet) appear on HHS’s public breach tool.
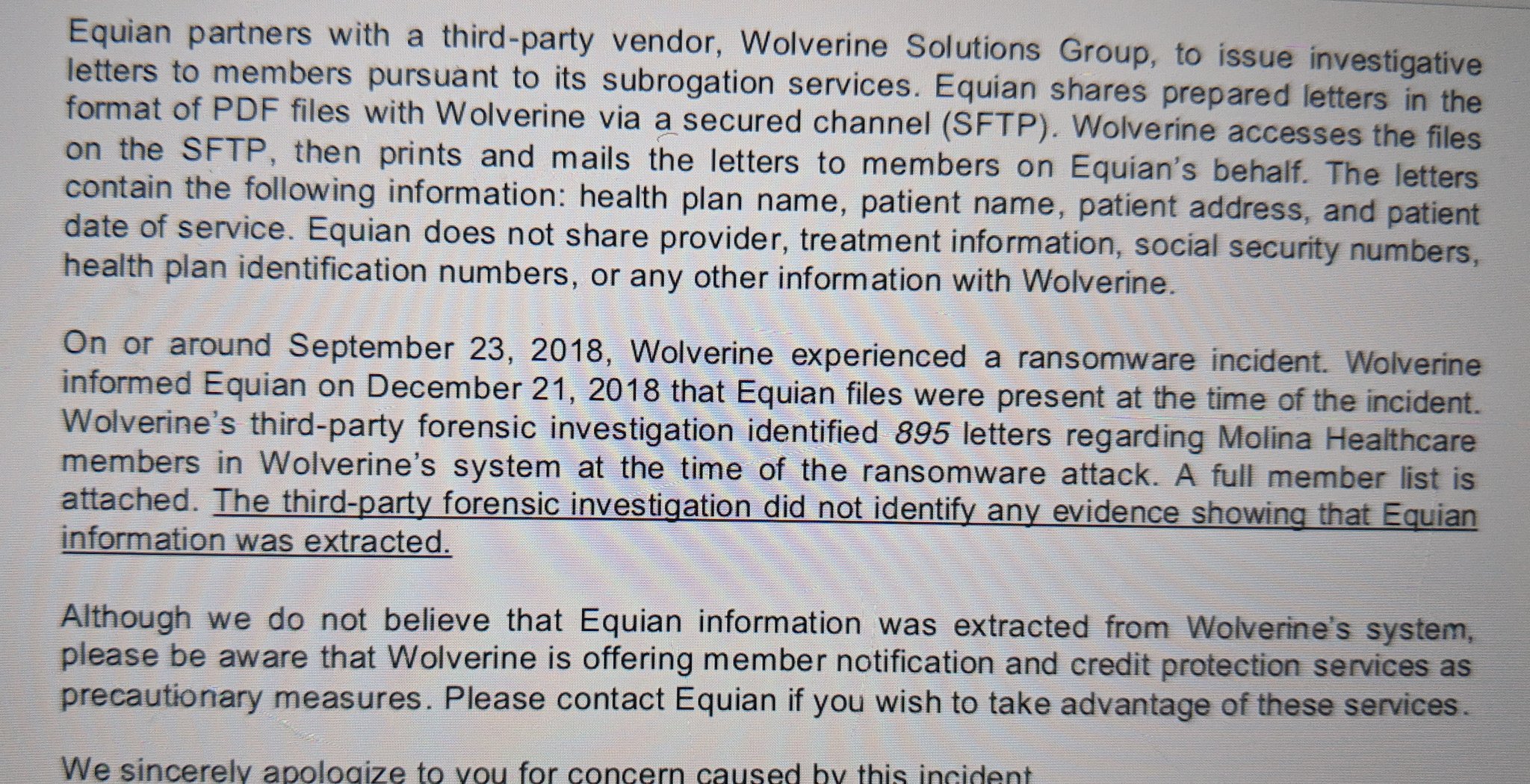
UPDATE: The Wolverine incident not only affected BCBS, but also affected other entities, as this screenshot from a notification referring to 895 Molina Healthcare patients indicates: