In early February, Berkeley County Schools in West Virginia experienced a ransomware attack. On March 3, the district issued a notice on its website that stated their investigation determined “some data stored in Berkeley County Schools’ network may have been accessed that included employee Social Security numbers and direct deposit information.”
That notice makes no mention of any student information being involved. The district reports they started mailing letters to affected individuals on March 10, but they do not indicate whether any of those letters are to former or current students or their families.
On March 10, Vice Society threat actors added Berkeley County Schools to their leak site.

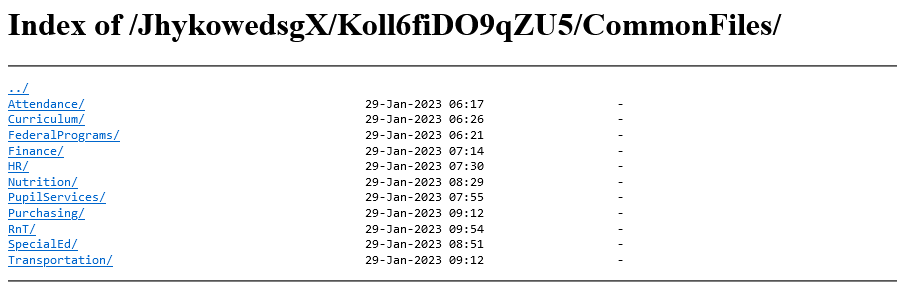
Even a cursory inspection of files in their data leak indicates that they acquired and have now leaked a lot of personal and sensitive information on students. Some of the files go back years.
As just one example, the following screencap, redacted by DataBreaches, shows a directory of files for named students who had FBAs and/or BIPs completed for them.
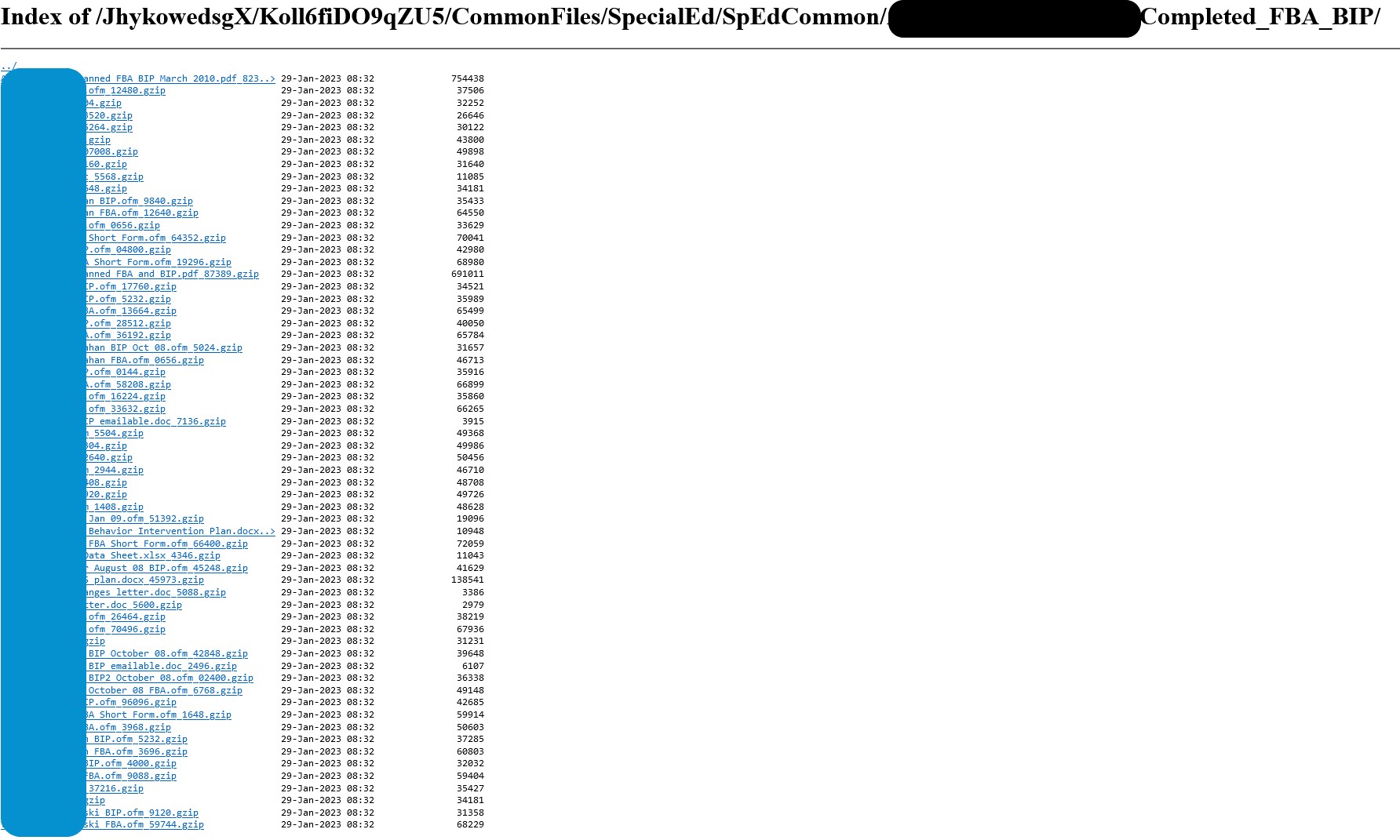
An FBA is a Functional Behavioral Assessment conducted to help school personnel identify what factors contribute to problematic behavior for a student and what factors might maintain it or mitigate it. The BIP is the Behavior Intervention Plan that the school develops to then address the problematic behavior. The FBA may contain sensitive information such as the student’s diagnoses, medications, home issues, or other factors.
In addition to files on FBAs/BIPs, DataBreaches also noted files with 504 Accommodation Plans for students with disabilities and other folders with pupils’ emergency contact information for the past decade or so.
There were also disciplinary matters. As one example, DataBreaches noted a letter to a parent in 2013 that informed her that the district was recommending that her son be expelled for one school year.
“I am taking this action for the following reasons,” the administrator wrote, because “On [date redacted by DataBreaches], 2013, [student’s name redacted by DataBreaches] was suspended from school for grabbing a fifth grade, female student in her genital area. He made sexual gestures toward the student, told her he “watches porn” and asked her to come to his house when his parents aren’t home so they could have sex. His previous disciplinary referrals this school year include: insubordination; use of profane language; making obscene gestures; disrupting class; failure to serve detention; battery against a student; disrespectful conduct; indecent act toward a school employee; and indecent act toward a student.”
Not all sensitive information in the leak concerned students, though. DataBreaches spotted one very sensitive harassment and bullying complaint filed by a school employee against two fellow school employees that described in painful detail their alleged physical abuse of a named and reportedly low-functioning disabled student. The report was filed in 2017.
The preceding are just a few examples of data in the leak. Berkeley County Schools needs to provide an accurate and full accounting of what files Vice Society accessed and acquired. This is much more than just some employee information. Former and current students and their families are also impacted by this breach.