Attacks on small to medium-sized medical entities continue, as this week’s breach posts unfortunately attest. Today, Vice Society added Atlanta Perinatal Associates in Georgia to its leak site. As they have done in the past, Vice Society did not just add the medical practice with a warning or threat. When Vice Society adds an entity, they simultaneously dump a copy of all the data they claim they exfiltrated.
Preliminary inspection of the leaked files reveals that they did not leak any major EMR system or billing system, but they appear to have accessed patient records such as ultrasound testing. The files appeared to be from 2019 to early April 2022.
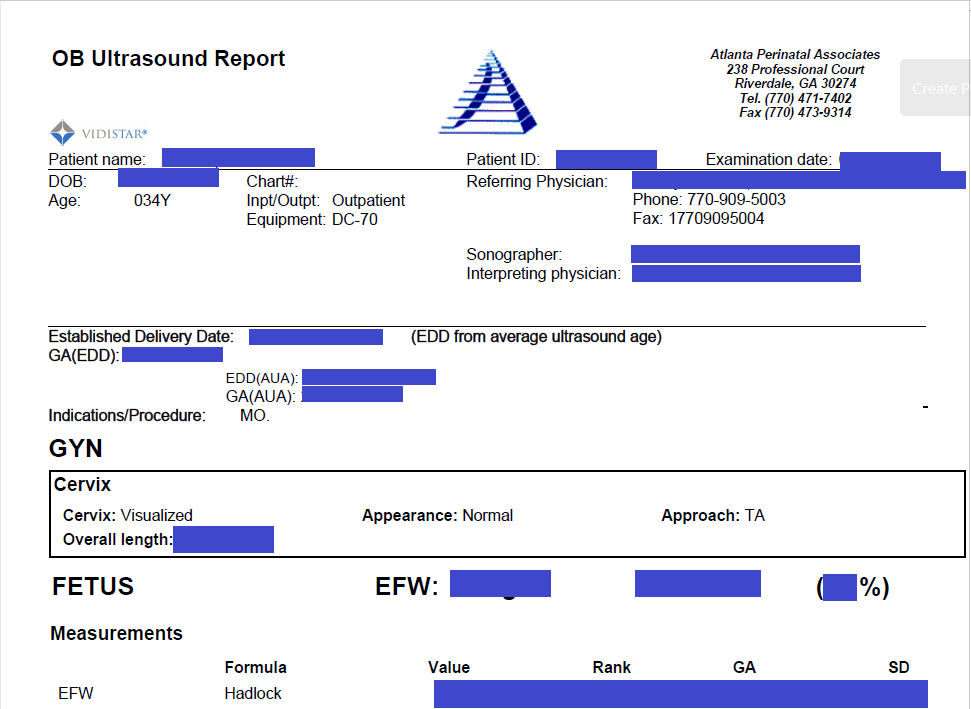
As is typical of ultrasound reports, the reports contain the patient’s name, date of birth, patient ID number, expected due date of delivery, referring physician, sonographer, and of course, the findings from the ultrasound. Each 6-page report also included the sonographer’s comments and detailed history with a review of systems, notation of any allergies, history of alcohol or smoking, family and social factors, and other health-related issues. The forms do not seem to include insurance information or Social Security numbers.
Other Obstetrics-related records were also found in the leaked files, as were files that included health insurance information. Yet other files included credit card information if the patient paid by credit card at the time of their visit or appointment.
Although the directory of folders included personnel-related or payroll-related folders, those folders appeared to be empty. A few direct deposit or payroll-related files were seen, however.
Atlanta Perinatal Associates was contacted via their website contact form earlier today but no reply has been received. DataBreaches also reached out to Vice Society via email to inquire whether they had encrypted Atlanta Perinatal’s files, and whether they could confirm that exfiltration occurred on or about April 9, 2022. This post will be updated if a response is received from either Atlanta Perinatal or Vice Society.